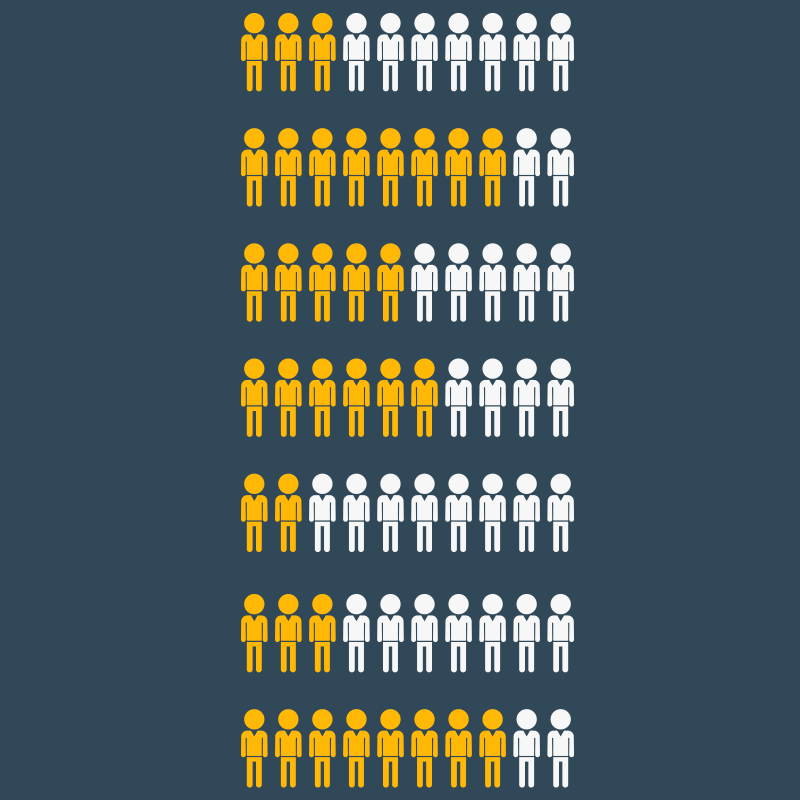
This is a story about an engineering group celebrating success when it shouldn’t be… and their organization buying into it. This is not the fault of the engineering groups, or the operations team, or any […]
Today’s Internet is powered by APIs. Tomorrow’s will be even more so. Without a pretty UI or a captivating experience, you’re judged simply on performance and availability. As an API provider, it is more critical […]
The Argument for Connectivity Agnosticism Turning the corner It’s about push vs. pull… but it shouldn’t be. There has been a lot of heated debate on whether pushing telemetry data from systems or pulling that […]
There is a class of problems in systems software that require guaranteed delivery of data from one stage of processing to the next stage of processing. In database systems, this usually involves a WAL file […]
Introducing Quick and Simple Onboarding with C:OSI When we started developing Circonus 6 years ago, we found many customers had very specific ideas about how they want their onboarding process to work. Since then, we’ve […]